| <<< Previous | Next >>> | |
Questions |
Question 1 : What is the operating system of the honeypot? How did you determine that? (see day1) |
|
The operating system of the honeypot is "Sun Solaris". This
result is obtained by using a passive OS fingerprinting tool and
confirmed by some others signs collected from the amount of packets
captured. |
Question 2 : How did the attacker(s) break into the system? (see day1) |
| The attacker (ip = 61.219.90.180) is exploiting a remotely
exploitable buffer overflow vulnerability in a shared library that is
used by dtspcd. More information can be found on the CERT website. Within the packet n° 580, the attacker has succeeded to send data to dtspcd and cause a buffer overflow, potentially executing code with root privileges. |
Question 3 : Which systems were used in this attack, and how?(see day1) |
Systems used in this attack are :
The psyBNC was successfully configured on port 7000 as the honeyport reported to the attacker over the packet # 8315. So, each system is using that port to communicate, it is potentially attacking the honeypot. These systems communicate using Gryphon protocol. The IRC traffic was generated then as a sequence to the Gryphon session. In fact, the attacker requested the honeypot to initiate IRC sessions which were been used in the attack. The following tethereal filter determine the involved systems. An other host is involved in this attack, which has the ip address : 80.117.14.44. The attacker communicates with the honeypot host using Gryphon protocol for the administration of psybnc. |
Question 4 : Create a diagram that demonstrates the sequences involved in the attack. (see day1) |
The following diagram shows the sequences involved in the
attack : 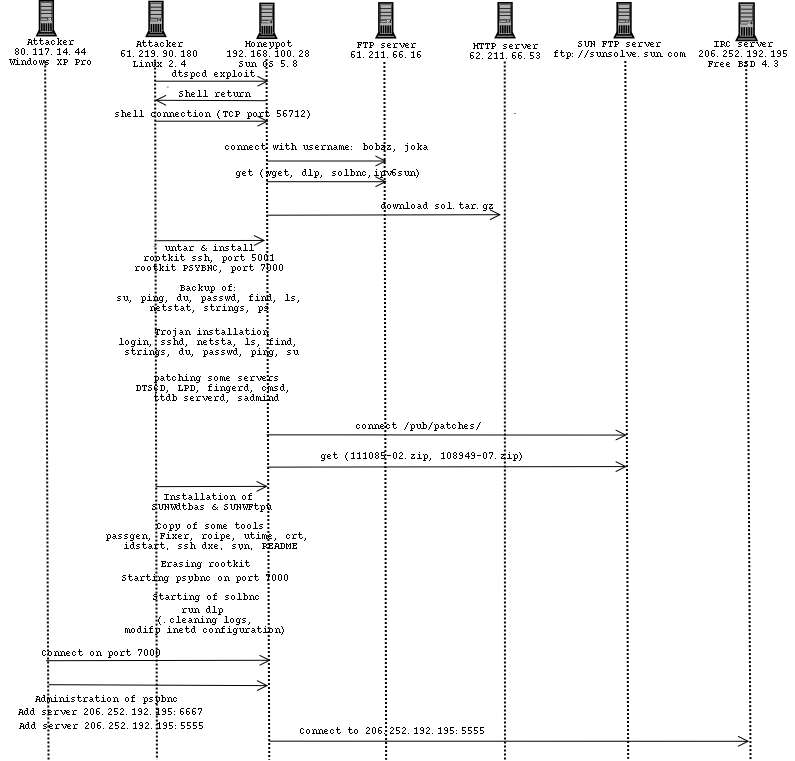 |
Question 5 : What is the purpose/reason of the ICMP packets with 'skillz' in them? (see day1) |
| This kind of ICMP
packets is the sign of an attack that is performed by a tool named Stacheldraht[1].
This tool performs a distributed denial of service attack (see
decription of Stacheldraht). This kind of icmp packets (icmp echo reply containing the string "skillz" ) is used to manage communications between handler and agent. The ICMP packets act as a "heartbeat" between agent and master server, and to determine source IP spoofing capabilities of the master server or handler. In this case, the two handlers has the following ip addresses :
|
Question 6 : Following the attack, the attacker(s) enabled a unique protocol that one would not expect to find on a n IPv4 network. Can you identify that protocol and why it was used? (see day3) |
| As we investigated firstly throw this analysis, the
day3.log lists the icmp v6 in addition to legitime carried IPv4
protocols. ICMP v6 datagrams are not expected network traffic. Hosts
generating ICMP v6 datagrams should be investigated for hostile
activity. The attacker enabled that protocol after compromising the
honeypot system. Attacking hosts use this protocol for Neighbor Discovery to determine the link-layer addresses for neighbors and to quickly purge cached values that become invalid. Hosts also use Neighbor Discovery to find neighboring routers that are willing to forward packets on their behalf. In IPv4 there is no generally agreed upon protocol or mechanism for Neighbor Unreachability Detection, although hosts Requirements does specify some possible algorithms for Dead Gateway Detection. So, the attacker enabled the use of this protocol meanly to detect peers which become unreachable. This techniques are used for neighbor solicitation. |
Question 7 : Can you identify the nationality of the attacker? (see day3) |
| To find what is the nationality of the attacker, specific
information need to be searched regardless of the involved techniques.
These information may be the communicating language of attacker, some
specific sentences, perhaps the addresses of the attacker. Within the day3.log, lot of IRC communication occured between the honeypot and 163.162.170.173 with encapsulated IPv6. The interchanged messages are formulated in Italian language. encora con bacardi? se rimango il pc acceso per molto tempo ... Perhaps, the attacker manipulates well Italian. All proofs, as it seems, indicate that the attacker has the Italian nationality even he is not really so. The irc server banner indicates that it accepts client requests only from *.it hosts. * Datagram n° 117631 : IPv6 I-lines are only for ItalianpTLA We do not discussI-lines for pTLA other than *.it The honeypot responses to the IRC client showing its host name (which is involved in the attack). * Datagram n° 117636 : your host is irc6.edisontel.it |
Bonus Questions |
Question 1 : What are the implications of using the unusual IP protocol to the Intrusion Detection industry? |
| The intrusion Detection industry must be able to
develop and implement solutions that can recognise traffic related to
this protocol. These modules or plugins should analyse this kind of
traffic to match available signatures or to be able to detect attacks
contained or encpasulted in ipv6 packets. |
Question 2 : What tools exist that can decode this protocol? |
| There are some decoders for ipv6. Ethereal from version 0.9.1 is able to decode v6 packets. Also, there are an "experimental" version of Snort with an IPv6 decoder. This decoder is implemented to test Snort's capability to analyze IPv6 and IPv6 tunneled over IPv4 |